Configuring SCIM User Provisioning with Entra ID
HP Insights supports automatically provisioning users and groups from Microsoft Entra ID using the System for Cross-domain Identity Management (SCIM) protocol. This document outlines the steps to configure Microsoft Entra ID to synchronize users and groups to HP Insights using SCIM.
Synchronization between HP Insights and Microsoft Entra ID supports the following:
- Create users or groups – Users and groups created in Microsoft Entra ID are added to the HP Insights.
- Update user attributes – Updates to user attributes in Microsoft Entra ID are synced to HP Insights
Note: Once a connection with SCIM is established, we do not recommend using the import function to import users into HP Insights. You can however use import to add cards for the users.
Note: SCIM with Microsoft Entra ID supports OpenID and SAML authentication type only.
Step 1: Generate SCIM Credentials in HP Insights Web Console
In this step, you will generate SCIM credentials in the HP Insights web console for use in Microsoft Entra ID.
1. In the HP Insights web console, navigate to the Account Settings > Settings tab.
2. In the User and Group Sync, click Generate Token.

3. The SCIM Credentials dialog appears.
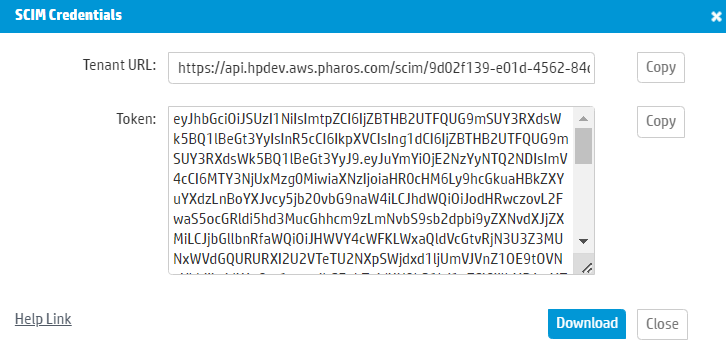
4. Download the Tenant URL and Token values. You will need these later when configuring the SCIM application in Entra ID.
Note: It is highly recommended to download a copy of the credentials using the Download button (instead of the Copy button). If you accidentally open a new tab, a new token will be generated and this may result in a mismatch.
Note: The Generate Token button changes to Regenerate Token if a token was already generated.
Note: The Token is valid for a year. If a token is about to expire or has expired, you will see an appropriate message in the HP Insights web console. You will need to regenerate a token and update the token in Microsoft Entra ID.
Step 2: Create a SCIM provisioning application in Microsoft Entra ID
1. Log in to the Microsoft Entra ID portal and select Microsoft Entra ID
2. Select Enterprise Applications and then click + New application.
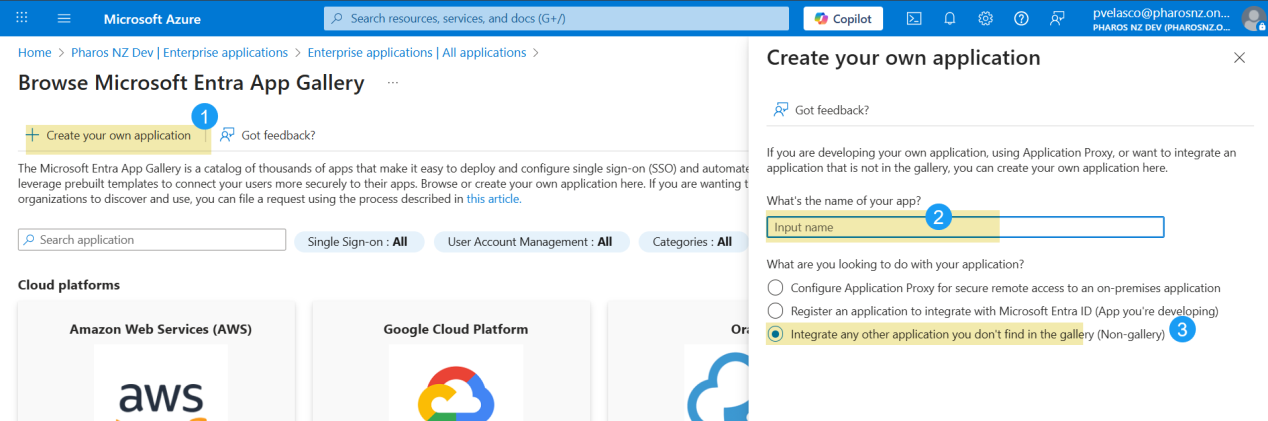
3. Select + Create your own application.
4. Enter a name for your application (for example, HP Insights SCIM). Select the option “Integrate any other application you don't find in the gallery" and select Create to create your application.
Step 3: Configure SCIM Provisioning in Microsoft Entra ID
1. In the Microsoft Entra ID portal, select the application you’ve just created if not already selected.
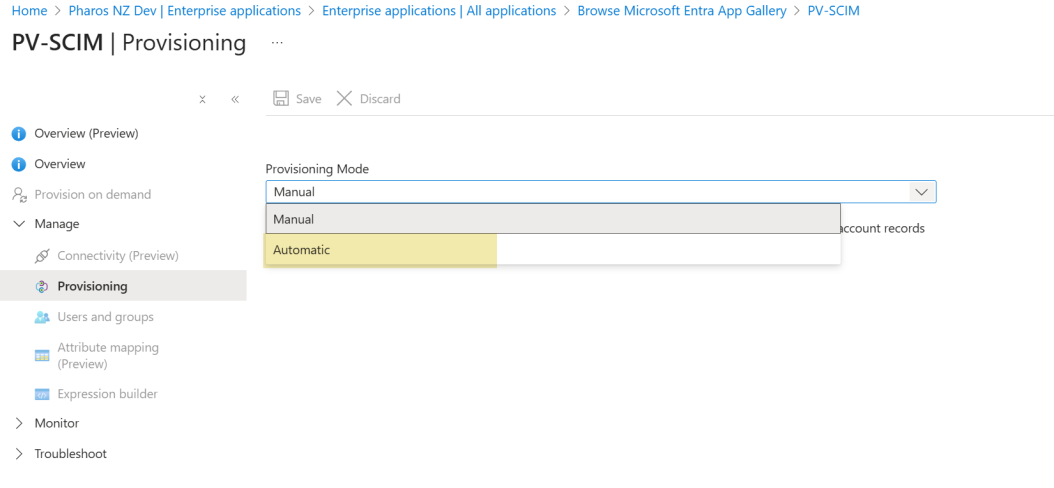
2. In the left-hand menu, select Provisioning
3. In the Provisioning Mode drop-down list box, select Automatic.
4. In the Tenant URL field, enter the URL of HP Insights's SCIM endpoint.
5. In the Secret Token field, enter the token generated from the HP Insights web console.
Note: Use the Tenant URL and Token values obtained in Step 1 of this document. You can get them from the Account Settings > Settings > User and Group Sync tab of the web console.
6. Click Test Connection to test whether the app can connect to HP Insights.
7. Select Save to save the Admin Credentials.
8. In the Mappings section, select Provision Azure Active Directory Users and start mapping attributes.
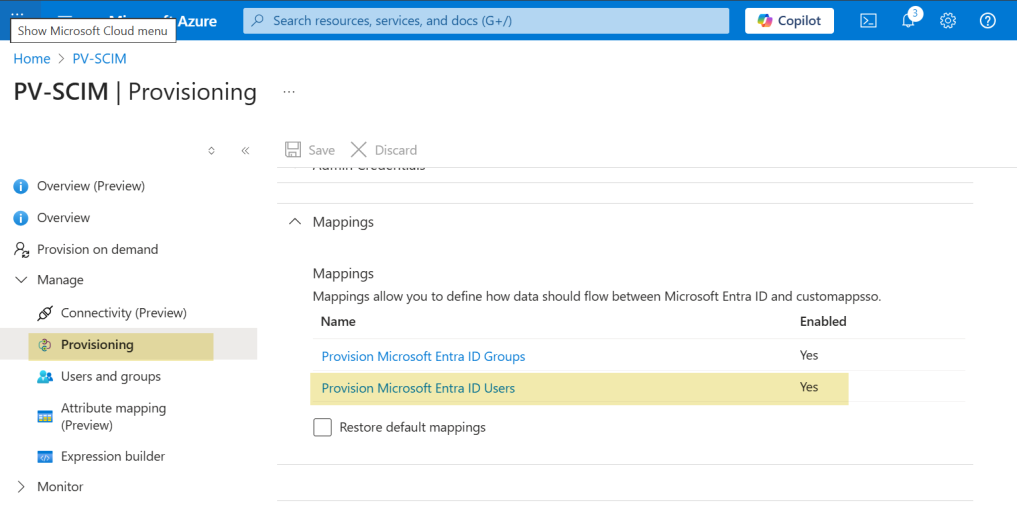
Note: Make sure that Create, Update, and Delete are selected.
9. On the page that appears, select the userPrincipalName and change the Matching precedence value to 2.
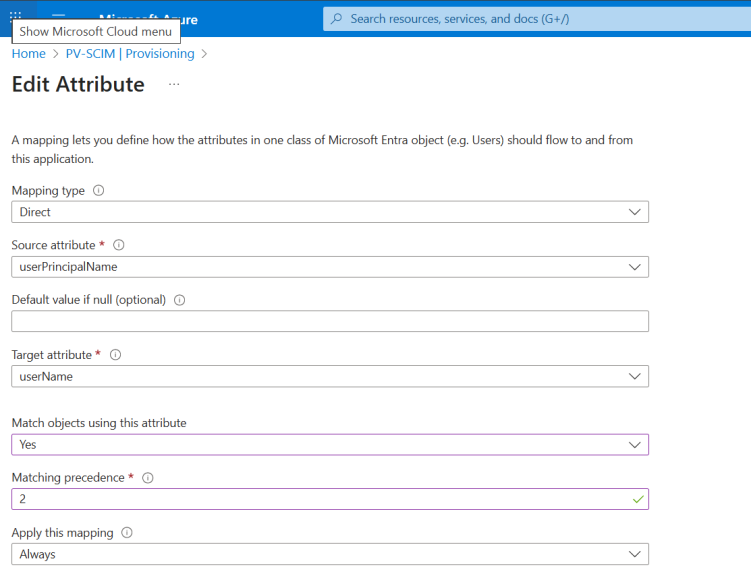
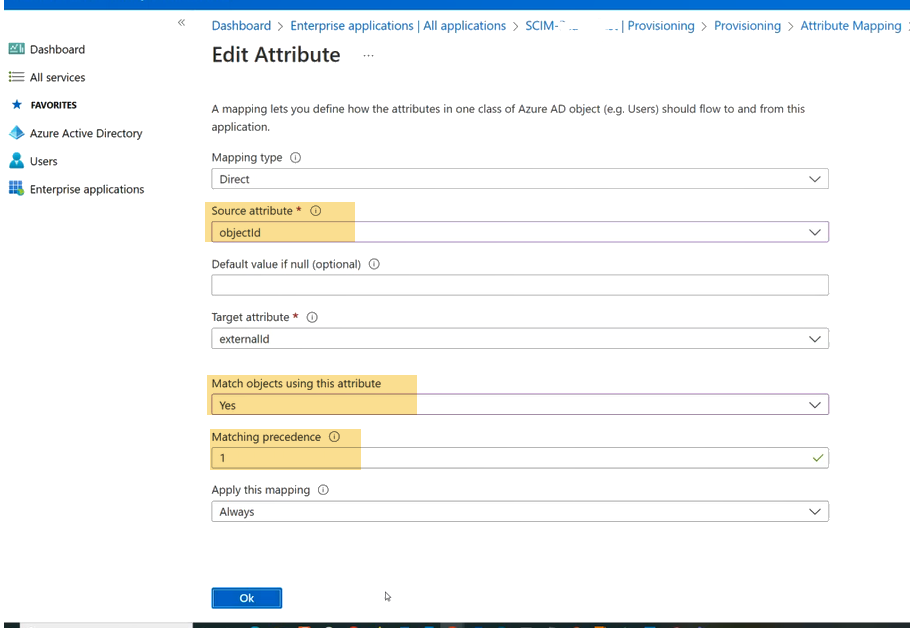
10. Select mailNickName, and change the following values:
- Set the Source attribute value to objectId.
- Set Match objects using this attribute to Yes. This sets the Matching precedence to 1. Click OK.
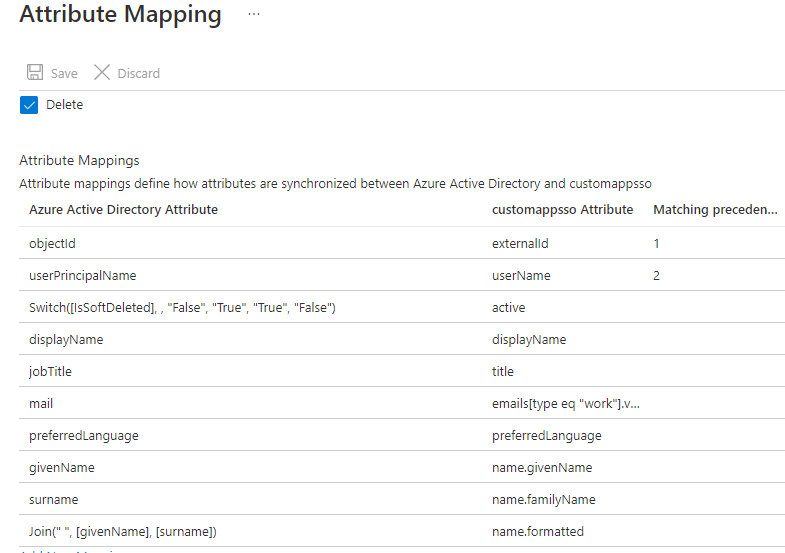
11. Keep the attribute mappings as shown below and delete all other attribute mappings. Your Attribute Mappings should match those listed below.
12. In the Settings section, set the Scope to “Sync only assigned users and groups”.
13. Set the Provisioning Status to ON.
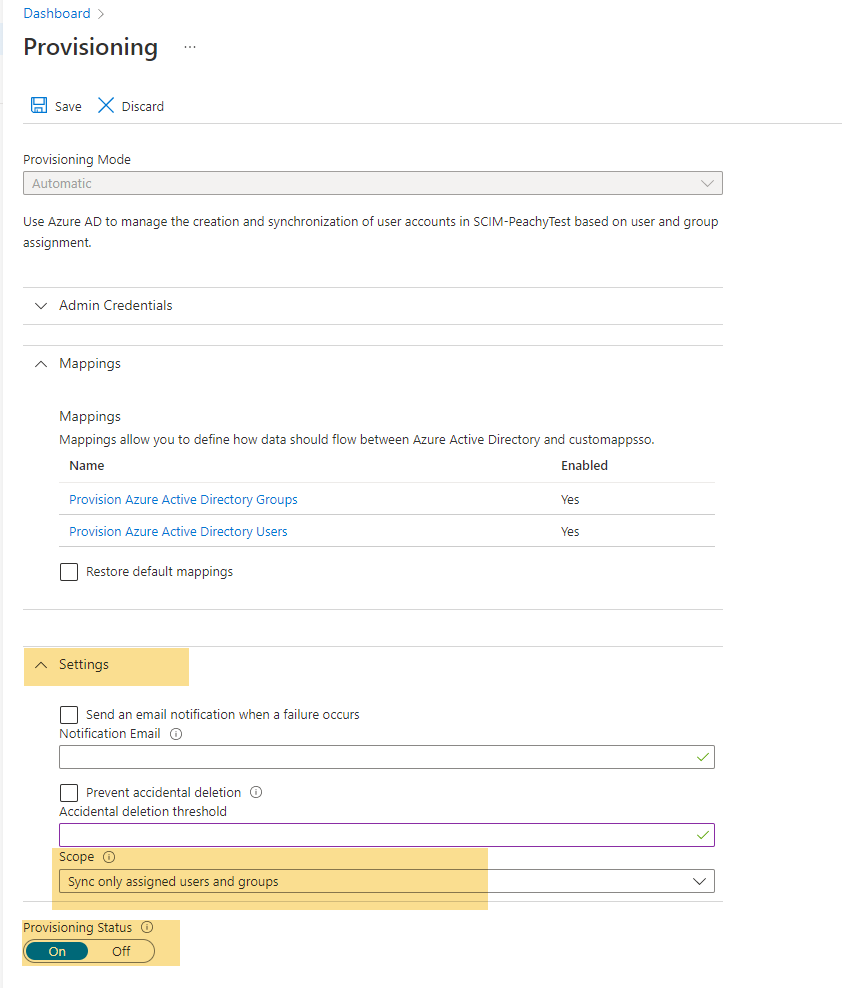
14. Save changes. This will start the Microsoft Entra ID provisioning service.
Note: Microsoft Entra ID runs synchronization every 40 minutes once a connection between HP Insights and Azure is established.
Step 4: Add Users and Groups
Navigate to the Users and Groups section of the app you’ve created in Azure and assign users or groups.
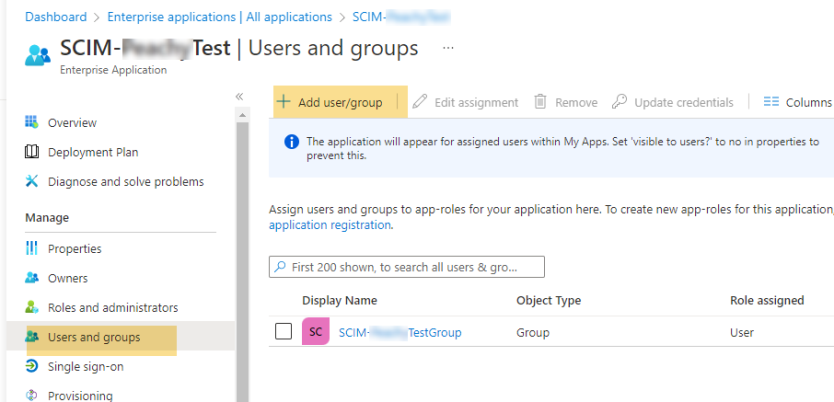
Note:
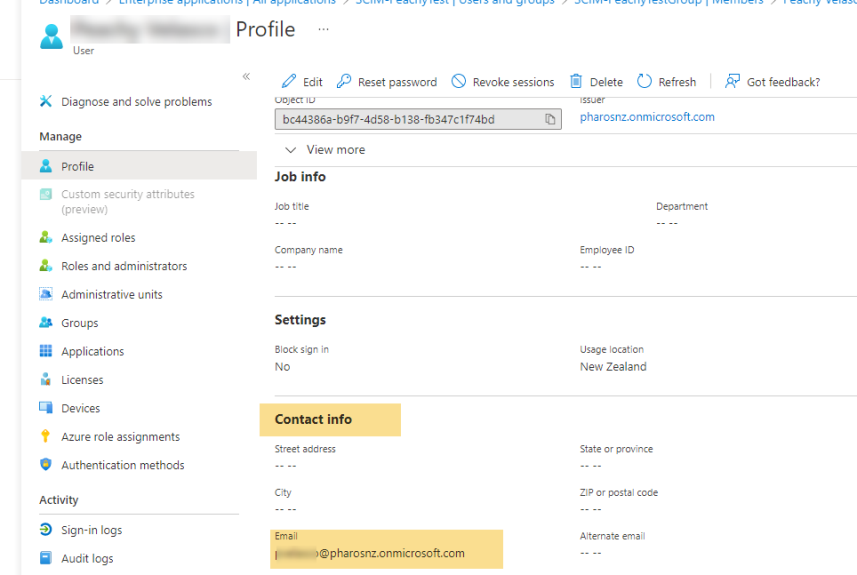
Users email address must be available in the contact info as shown below.